Lists of frequently asked questions
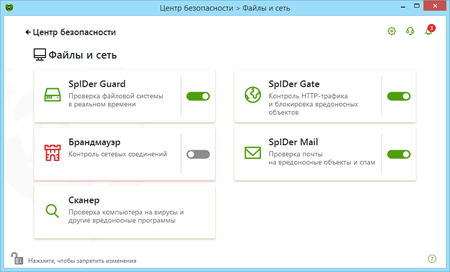
Protection components and how to configure them
Program components
Can I disable SpIDer Mail? After all, doesn’t the scanner also check email files?
Dr.Web Scanner can detect viruses in some mailboxes, but SpIDer Mail has a number of advantages:
- Not all popular mailbox formats are supported by Dr.Web Scanner, and if you use SpIDer Mail, infected emails do not even reach mailboxes;
- Dr.Web Scanner scans mailboxes, but only at the user's request or on a schedule, and not while a mail client is retrieving emails; and this action is very resource consuming and takes a considerable amount of time.
Thus, when all the Dr.Web components are configured with their default settings, SpIDer Mail is the first to detect viruses and prevent them and suspicious objects spread via email from reaching your computer. Its operation is highly advantageous in terms of computing resources; the remaining components don’t need to be used to scan email files.
I have a strong suspicion that a virus has gotten into my computer. How can I run the scanner?
There are several ways to start the scanner.
- On the desktop, find the icon with the spider on a green background — Dr.Web Scanner. Double-click the scanner to run it.
- Open the Dr.Web menu (right-click on the Dr.Web icon in the system tray) and select Security Center. Next, select Files and Network, and then Scanner. Select the desired scanning mode: express, full, or custom.
- To scan a specific object (file or folder), right-click on it. In the context menu, select Scan with Dr.Web (the icon with the black spider on a grey background). The Scanner will start immediately, and the file will be scanned.
I use a very rare email program. In this case, will one of the anti-virus components — SpIDerMail — protect my system?
SpIDer Mail will scan both incoming and outgoing mail on your computer, regardless of which mail client you use.
In the scanner settings, there is the option to process suspicious and incurable files — Move to quarantine. Are those files moved to some place on my computer? That is, does it remain infected with a virus?
The Move action for suspicious and incurable objects means the file is moved to a special quarantine folder. After having been moved, the file loses its extension. This means the virus has literally been disarmed and rendered non-operational and, therefore, harmless. Later, you can open the Quarantine Manager (Security Center → Tools → Quarantine Manager) and delete the files if you do not need them.
Dr.Web Security Space for Windows includes many components. Which of them actually protect my system against viruses, and which are only subsidiary?
The Dr.Web anti-virus is a set of programs (modules), each of which is responsible for protecting its own section of your computer. Removing (making unavailable) or disabling at least one component greatly reduces the overall reliability of the anti-virus protection, so we strongly advise you not to disable any of its modules unless absolutely necessary.
The Automatic Updating Utility and the Scheduler included in the comprehensive anti-virus are subsidiary programs.
Dr.Web simply deletes trojans but doesn't cure them?
To answer this question, you need to understand the difference between an object infected by viruses and malicious software.
Typically, a virus adds (appends its code) to an infected file so it incorporates its own code and the virus's code. Together, they represent a virus-infected file. Most of these files can be cured (and are cured) by Dr.Web anti-virus. Here we are speaking about curing files of viruses rather than curing viruses.
Malicious software in itself operates as a separate computer program, so it cannot be cured but only removed. In some cases, we can speak about curing a system (but not malicious software). This includes removing the detected threat and restoring the compromised objects.
Settings
How can I configure Dr.Web so that I can access the protected system remotely?
Dr.Web for Windows 11.5:
- Click on the Dr.Web icon in the notification area (in the lower-right corner of the screen).
- Click on the padlock icon (Administrative mode) to allow the application to launch.
- Click on the gear icon (Settings), and then click on General → Self-protection.
- Toggle off the Block user activity emulation option.
Dr.Web for Windows 12:
- Click on the Dr.Web icon in the notification area (in the lower-right corner of the screen).
- Select Security Center, and click on the padlock icon (Administrative mode) to allow the settings to be changed.
- Click on the gear icon (Settings) in the top-right corner of the installer window, and then click on Self-protection.
- Toggle off the Block user activity emulation option.
You can also toggle off this option during the anti-virus installation process in the Installation parameters section — in the Advanced options tab.
How can I boot in Windows safe mode?
To enter the safe mode when your PC is booting, press F8 at the moment the computer vendor picture disappears, before Windows logo is displayed. If you can see the Windows logo then you failed to press the button in time. In this case, you need to wait for the Windows system login window to appear, shut down and reboot your PC.
If you managed to press F8 key in time, you will see the Windows boot menu on the screen.
Use arrow keys to select a boot mode you need, and press Enter.
How can I check and change the system date?
To check the date, roll the mouse cursor over the clock icon in the notification area. The system date will be displayed in the pop-up hint. To change the date, do the following: right-click on the clock icon in the notifications area and select Date/time settings in the open menu. In the next window, set the current date and press Ok.
How can I create a Windows XP system registry archive copy?
Press Start–>All programs–>Standard–>Service–>Data archving. The archiving window appears. Press Next, check the Archive files and parameters in the next window and press Next. In the next window, select Allow choosing objects to be archived and press Next. Now, open My computer in the left-hand part of the window, check System State box and press Next. Specify archive file save path and name. Verify the data displayed and press Ready. When the operation is completed, you may close the archiver window.
How can I enable the Scheduler?
Locate the C:\WINDOWS\inf\mstask.inf file right-click it and select Install item. During installation, you might need an OS installation disk. Your PC may need to reboot.
How can I export a registry tree?
press Start–>Run and enter the the following command in the open line
reg export "tree" file namewhere the “tree” is the registry tree you need to export (tree should be embraced with quotes);
file name is the file where the result will be saved.
For example, you need to export the
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control tree into the C:\result.reg fileThe command will be as follows
reg export "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control" c:\result.reg
How can I know my Windows version?
Press Start–>Run and enter the winver command in the open line.
How can I reset Internet connection settings?
To reset Internet connection settings, press Start–>Run and enter the following command in the open line:
netsh winsock reset
And press Ok.
Note: to restore your previous settings, export the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WinSock2 registry tree prior to reset.
I cannor launch an *.exe application. What am I to do?
If the system recovery is enabled on your PC then roll back the system to a checkpoint when this problem did not exist.
If this measure was useless or the system recovery is disabled then try to use a utility located at plstfix.exe.
The disk will not open after viruses have been cured. What am I to do?
Try to use a utility located at plstfix.exe
What is a ticket?
A ticket is a virtual document keeping technical support calls and dialogs between an engineer an user.
What is md5 and how can I get it?
It is a file checksum required to confirm data integrity and authenticity. To get the checksum, use the Hash program or visit forum.drweb.com/hash. When linking, select the file you need with the Browse button and press Compute. When the analysis is over, you will be provided with all the file information, including md5.
Why cannot I install two anti-viruses on one PC?
It is not allowed to install several anti-virus programs on one PC at a time — they will conflict with each other that may considerably slow down you PC or make it completely non-operational. If you have an anti-virus software already installed on your PC, but intend to install a new product from another vendor, then you need to remove the anti-virus program you have, prior to the installation.
If you wish to install another anti-virus program, you do it at your own risk, and become responsible for all the consequences because the consequences of such installation might be unpredictable including inability of your OS to boot as a result of two or more anti-viruses installed on your PC.
I forgot the password for my anti-virus—how can I recover it?
These instructions are intended for users of Dr.Web Security Suite and current versions of Dr.Web Anti-virus for Windows.
Dr.Web technologies are designed to prevent user data, including passwords, from being obtained by hackers. The password is not stored in plain text, so it cannot be recovered.
In addition, Doctor Web does not collect the personal data of Dr.Web users, and, therefore, passwords cannot be recovered by contacting our technical support service.
You have to reinstall the product you are using so that you can gain access to the anti-virus’s settings. Once you do this, all the settings you previously configured, including your password, will be lost.
- Save the Dr.Web key file (this file has the .key extension and contains information about your license). The file can be found in the directory C:\Program Files\DrWeb. For example, put it on your desktop.
- To reinstall Dr.Web, you will need its distribution. Download it in the Download Wizard. Enter your serial number or your key file—the file with the extension .key that contains information about your license (you can find it in the directory C:\Program Files\DrWeb)—and your registered email address, and then click on the Download button. In the newly appeared window, the download option for Windows and Android is already selected, so you can just click on the Send button. In the next dialogue box, select the download version:
- 11.5 if you are already using Windows XP;
- 12 if you are using Windows Vista and later versions.
Dr.Web does not support versions below Windows XP.
Download the Dr.Web distribution.
Remove the anti-virus.
Go to the Control Panel, and select Start → Search → Control Panel. After this, depending on the type of Control Panel you have — Programs and Features or Remove program.
In the list of programs, select Dr.Web Anti-virus or Dr.Web Security Space. Click on Remove, and follow the Removal Wizard's instructions.
In the Parameters to save window, clear the checkbox next to Settings.
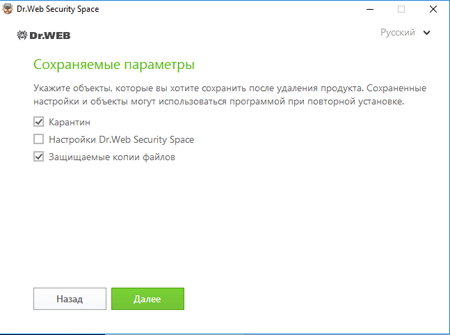
After you remove the solution, restart the computer, and reinstall Dr.Web. Your key file will be downloaded automatically.
If the key file is not downloaded automatically during the installation, enter it manually. To do this, in the anti-virus's menu, select Licenses. In the License Manager window, click on the Buy or activate new license button. Then click on the text or specify the key file, and select the previously saved key file — the desktop file that begins with SL and has the .key extension.
If a proxy server is used to access the network—do I somehow need to configure the update procedure for Dr.Web Security Space?
Yes, you need to specify the proxy server you are using in the Dr.Web Security Space settings.
- Click on the Dr.Web icon
 in the notification area (in the lower-right corner of your screen).
in the notification area (in the lower-right corner of your screen). - Select "Dr.Web Security Center" and then the padlock icon
 (Administrative mode) in the lower-left corner of the window; to ensure the settings can be accessed, allow the launch of the application.
(Administrative mode) in the lower-left corner of the window; to ensure the settings can be accessed, allow the launch of the application. - If you set a password to access the settings — enter it.
- The icon in the lower-left corner of the window will change to
 .
. - Click on the gear icon
 (Settings) in the top-right corner of the window, and click on Network.
(Settings) in the top-right corner of the window, and click on Network. - After clicking, toggle the switch Use proxy server to the On position. If the proxy server settings were not previously set up, the Proxy server parameters 6. window will automatically open. Otherwise, click on Change.
- Specify the connection parameters
Can I change the Dr.Web Security Space settings (such as the proxy server parameters) without having administrator privileges?
No, for security reasons. If no restrictions are placed on accessing the settings, cybercriminals could change the anti-virus’s settings to block its operation.
How do I find the Security Center?
Click on the Dr.Web icon ![]() in the notification area (in the lower-right corner of your screen). If the icon is not displayed in the tray, click on the “up arrow” button
in the notification area (in the lower-right corner of your screen). If the icon is not displayed in the tray, click on the “up arrow” button

and in the newly opened panel, click on the Dr.Web icon ![]() .
.

! The appearance of the “up arrow” may vary depending on the OS version and its settings. For example, it may look like  or
or  .
.
Click on “Security Center”

If the button ![]() is not displayed (it can be hidden by your network administrator), contact your system administrator or use the “Start” button to launch the Security Center.
is not displayed (it can be hidden by your network administrator), contact your system administrator or use the “Start” button to launch the Security Center.
Click on the “Start” button (its appearance may vary depending on your OS version, but it is usually displayed in the lower-left corner of the screen)

Click on "Dr.Web", and in the newly appeared list, click on "Security Center"
The “Security Center” window will open. The list of contents may vary depending on your product version.
The list of available options may vary depending on your product version and the settings configured by your network administrator.
By default, the changing of settings is disabled. To change them, click on the padlock icon  (Administrative mode) in the lower-left corner of the window. If you set a password to access the settings — enter it.
(Administrative mode) in the lower-left corner of the window. If you set a password to access the settings — enter it.
The icon in the lower-left corner of the window will change to  .
.
Preventive Protection
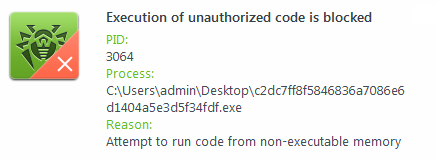
What does this message mean: "Execution of unauthorized code is blocked"?
Dr.Web Anti-virus can not only detect known malicious programs but also block the actions of the latest tools used by hackers. Dr.Web Preventive Protection monitors the requests all running programs make of various system resources and, with the help of special rules, identifies actions that are atypical of legitimate programs. In this case, the message indicates that an attempt was made to inject some code into a running process — legitimate programs rarely act in such a way.
Thus, Dr.Web Anti-virus has blocked hackers from using the computer’s unclosed vulnerability.
To avoid such situations, you need to install all the security updates released by Microsoft to date in the system where the malicious action is being detected. After this, reboot your PC.
You must also ensure that the Dr.Web components are up to date and that the virus databases show today’s date.
To detect threats, in the Dr.Web Preventive Protection settings, select Ask as the action for the option Integrity of running applications, and also enable exploit protection interactive mode.
Contact our technical support. Attach to the request a report from the system in which the anti-virus is installed. To do this, right-click on the Dr.Web icon in the system tray, open Security Center -> Support  , click on "Go to Report Wizard", and then click on "Create report". Wait for the report-generation process to complete. A file with a .zip extension is generated—attach it to your request.
, click on "Go to Report Wizard", and then click on "Create report". Wait for the report-generation process to complete. A file with a .zip extension is generated—attach it to your request.
The Dr.Web Report Wizard (the dwsysinfo application) is a special Dr.Web utility for collecting system information. The utility generates a zip archive containing event logs, XML documents, the HOSTS file, and other information. The full list of data available in the report can be found here.
HTTP monitor SpIDer Gate
A connection failure occurs when I try to download a program. If I turn off SpIDer Gate, downloading continues without interruptions. What shall I do?
Try running SpIDer Gate with the -dbg: 2 parameter. To do this, click Start-> Run, type in the string provided below:
"C:\Program Files\DrWeb\spidergate.exe" –dbg:2
Click Ok.
If the problem persists, please contact the technical support service.
Can the firewall do Spider Gate's work?
No, SpIDer Gate is an HTTP-monitor. It performs the following tasks:
- Scan incoming and outgoing HTTP-traffic
- Intercept all HTTP-connections
- Filter Data
- Block loading infected pages automatically in any browser
- Scan archived files
- Protect from phishing and other dangerous online resources.
At the same time the firewall protects your PC or network from unauthorized access.
Thus, SpIDer Gate and the firewall must operate simultaneously on your computer to protect your system against viruses and network attacks.
Does SpIDer Gate depend on my browser?
No. SpIDer Gate operates independently of the programs that use the Internet (including browsers).
Does operation of SpIDer Gate slow down web surfing?
Dr.Web anti-virus engine is so fast that SpIDer Gate won’t delay loading of web-pages or slow-down file transfers.
How can I configure SpIDer Gate's verbose log?
For version 5.0:
- Increase log file size up to 5 Megabytes. Right-click on the Dr.Web icon in the notifications area, select SpIDer Gate–>Settings, in the next window proceed to the Log tab and modify the File size limit field value.
- Right-click on the Dr.Web icon in the notifications area and select SpIDer Gate ->Disable.
- Press Start–>Run, copy one of the strings below to the Run field and launch SpIDer Gate:
- "C:\Program Files\DrWeb\spidergate.exe" -dbg — enable verbose logging,
- "C:\Program Files\DrWeb\spidergate.exe" -dbg -dbg — debug logging.
Version 6.0
Right-click on the Dr.Web icon in the notifications area and select SpIDer Gate–>Settings from the list (if this item is unavailable, you should first switch to the Administrator mode). In the next window, open the Log section and use the slider to set the Extended mode. Press Ok to confirm the changes made.
Further, if required, you can reproduce the problem that must be analysed using the extended report. Please keep in mind that the Debug log is not always required because redundant information might complicate troubleshooting.
How can I disable the SpIDer Gate HTTP monitor?
It is not recommended to disable the SpIDer Gate HTTP monitor because nowadays a lot of malware is distributed via infected websites. There are many script viruses and exploits that can cause harm to the system before they are saved to your hard drive and, consequently, detected by the SpIDer Guard® file monitor.
If disabling HTTP monitor is still necessary, right-click on the Dr.Web icon and in the next menu, select SpIDer Gate –> Disable. When anti-virus self-protection screen appears, type digits from the picture into the string and click Disable SpIDer Gate.
How do I disable the HTTP-monitor SpIDer Gate?
Right-click on the Dr.Web icon in the system tray and select SpIDer Gate-> Disable in the context menu.
Caution! It is not recommended to disable the HTTP-monitor SpIDer Gate because nowadays a lot of malware is distributed via infected web sites. There are many script viruses and exploits that can harm the system before they are saved to your hard drive and, consequently, detected by the file monitor SpIDer Guard.
How do I update the HTTP-monitor SpIDer Gate?
Since SpIDer Gate utilizes the Dr.Web engine and databases, it is updated automatically along with other anti-virus modules.
How is SpIDer Gate updated?
As other modules of the program Dr.Web, SpIDer Gate features the same anti-virus engine and uses the same virus databases and therefore is updated along with other modules.
The SpIDer Gate icon is red. What shall I do?
The red icon indicates that SpIDer Gate is disabled. To activate it, right click on the Dr.Web icon in the notification area. In the menu, hover over the SpIDer Gate item and in the drop-down list select Enable.
If the icon remains red, you have two options:
- Application error – in this case you need to contact the Technical support service.
- Your license does not cover SpIDer Gate. In this case, it is recommended to remove the component: Go to Start-> Settings-> Control Panel-> Add and Remove Programs, find the Dr.Web anti-virus on the list, click Modify and follow the wizard's instructions to disable this component.
What is the impact of SpIDer Gate on the web-surfing speed?
The unique Dr.Web anti-virus engine allows SpIDer Gate to scan traffic so quickly that you will never notice any delay when viewing web pages and downloading files from the Internet.
When I try to go to some sites, SpIDer Gate blocks them and displays the message "URL is known as a source of infection." How can I disable this feature?
If you believe that SpIDer Gate has mistakenly blocked a respected site, please let us know through the form on our website.
If you need to access a suspicious site, right click on the Dr.Web icon in the system tray and in the context menu select SpIDer Gate-> Settings. Clear the Block known source check box and press Ok.
Caution! Disabling this option is not recommended, because pages from all sites, including potentially dangerous ones will be loaded without a corresponding warning.
Where can I find SpIDer Gate's log?
SpIDer Gate's log file name is spidergate.log. The file is located in the C:\Documents and Settings\Your_user_name\DoctorWeb folder.
Which browsers support SpIDer Gate?
SpIDer Gate is compatible with all web-browsers.
Dr.Web anti-virus engine is so fast that SpIDer Gate won’t delay loading of web-pages or slow-down file transfers.
Why do I need the Speed balance option?
The Speed balance option allows you to adjust the amount of CPU time utilized to scan Internet traffic. The higher the scanning priority, the more CPU resources it will use, but it will help maintain high speed connectivity. Low priority results in low CPU load and slower network communication speed. Changing the default value usually is not required.
Why does Dr.Web Security Space literally devour traffic? The dwnetfilter anti-virus component’s traffic exceeds all the remaining Internet traffic.
In fact, the component does not consume traffic. The component checks it while passing it through itself. It processes as much traffic as is generated by the applications that have accessed the Internet and the data that has been received/sent over the network.
Technically, it looks like this:
To check traffic, the anti-virus installs its Internet traffic filters in the protected system and presents itself as a proxy. This filter must be the very first one so that malware cannot process the traffic before it does. For example, in order to conceal that it is transferring data. Third-party monitoring systems also install similar counting filters, but they process traffic after the anti-virus filter because such filters always work consistently. That's why the dwnetfilter process will always be seen as the main consumer of traffic.
On its own initiative, the dwnetfilter component does not connect to the Internet, it only intercepts connections from other applications.
To exclude the false effect that the dwnetfilter component is consuming traffic, you need to exclude it from your traffic control program, if this option is available. It makes no sense to track application traffic separately or their total traffic via the proxy (dwnetfilter).
This script should be used to answer users’ questions.
One of SpIDer Gate’s tasks is to inform users that visiting some websites is dangerous or undesirable, for reasons that include the presence of “pirated” content. Dr.Web informs users about such websites because they are accompanied by malicious programs. Websites are included in the so-called Dr.Web “anti-piracy” database only on the basis of allegations made by content copyright holders. Each allegation is verified by Doctor Web’s lawyers before the decision is made to include the corresponding URL in the database. When users receive SpIDer Gate notifications concerning the undesirability of visiting pirated websites, they are getting objective, legally considered information about intellectual property infringement. Thus, Doctor Web helps users of its products:
- avoid becoming the victims of criminals, who for their own selfish ends use others’ works and trademarks, and the fruits of others’ intellectual labours, for illegal purposes;
- avoid potential criminal indictment for downloading, using, and further distributing pirated content;
- protect PCs against infections occurring as a result of downloading unlicensed content that is accompanied by malicious programs.
Users make their own decisions as to whether it is worth visiting the websites they have been notified about. The SpIDer Gate component can be enabled or disabled at their discretion.
How to add a site to SpIDer Gate's exclusions list for Windows
Click on the Dr.Web icon in the system tray.
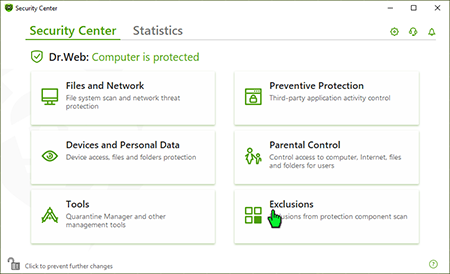
Open the Dr.Web Security Center.
Windows administrator permissions are required for changes to be made to Dr.Web’s settings. Click on the padlock icon to provide them.
Confirm the system prompt to elevate privileges to those of an administrator.
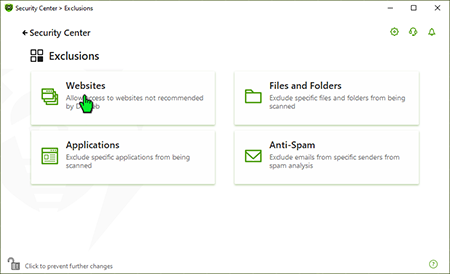
Click on "Exclusions".
Click on "Websites".
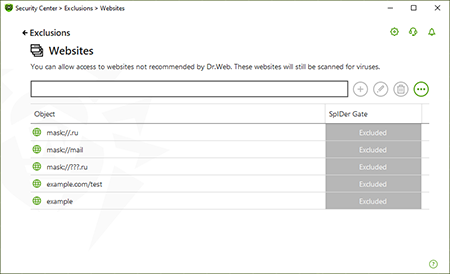
Add the URLs to which you want to allow access. After entering a site address, click on the "+" button.
To add a specific site to the list, enter its address (for example, www.example.com). Access to all the resources located on this site, will be allowed.
To allow access to sites whose address contains a specific text, type the following text in the field. Example: if you enter the text "example", access to example.com, example.test.com, test.com/example, test.example222.ru, etc., will be allowed;
To allow access to a specific domain, specify the domain name with the symbol ".". In this case, access to all the resources on that domain will be allowed. If you use the symbol "/" when specifying a domain, the part of the substring to the left of the character "/" will be considered the domain name, and the part to the right of the symbol—the part of the allowed address on this domain. Example: if you enter the text example.com/test, the following addresses will be allowed: example.com/test11, template.example.com/test22, etc .;
To exclude certain sites from scanning, enter the corresponding mask. Masks are added in the format: mask://...
The mask specifies the name pattern:
- the symbol "*" replaces any, possibly empty, sequence of characters;
- the symbol "?" replaces any, including empty, but only one symbol.
Examples:
mask://*.ru/ — all sites in the .ru zone will open;
mask://mail — all sites containing the word "mail" will open;
mask://???.ru/ — all sites in the .ru zone whose names consist of 3 or more characters will open.
When added onto the list, an entered string can be converted to the universal form. For example, http://www.example.com will be converted to www.example.com.
Parental control
How can I use the Parental Control component in Dr.Web for Windows to restrict access to unwanted sites?
- Click on the spider image in the system tray.
- Click on the closed padlock icon—the system will request elevated privileges.
- Agree, and, if necessary, enter the administrator account password. The closed padlock is now open.
- Click on the gear icon.
- In the Dr.Web settings window, open the Parental Control tab.
- In the section on the right, select the user account for which you want to set restrictions.
- Click on Change in the Internet section.
- In the drop-down list, select Block by categories.
- Select the categories of the sites you want to block.
Doctor Web specialists are continuously adding sites to the list for each category. How they do this is described in this Moscow News article.
Find out more
How can I grant my child access to specific sites belonging to one of the blocked categories or expand the list of blocked sites?
- Go to the Parental Control tab.
- In the section on the right, select the user account for which you want to set restrictions.
- Click on Change in the Internet section.
- Select Block by categories
- Click on the button Whitelists and blacklists.
- To make sure that access to a certain site is not blocked, add its address to the whitelist.
- To add a site to the list of unwanted sites, add its address to the blacklist.
- If you want the user to access only specific sites, add the site addresses to the whitelist and choose the option Block all except websites from the whitelist.
Popular search engines, such as Google and Yandex, offer a safe search option that enables links to sites containing dangerous or unwanted content to be excluded from search results. So that the browser toggles on the safe search option automatically, enable the corresponding Parental Control feature.
Find out more
How can I use the Parental Control component in Dr.Web for Windows to block access to selected files and folders?
- Open the Files and Folders tab, and click on the switch.
- Add the paths to the files and folders to the list, and select an access mode.
If you choose Read-only, your child will be able to view files and folder contents but won't be able to change or delete them.
The Blocked option will mean that the files and folders will be inaccessible.
How can I prevent third parties from making changes to the Parental Control settings in Dr.Web for Windows?
- Select Start → Settings.
- Go to the Accounts section.
- Click on Family and other users.
- Make sure the user accounts for which you have imposed the restrictions do not have administrator privileges.
- If necessary, change their account type from Administrator to Standard.
- Also make sure that a reliable password is specified for your Administrator account. If no password is specified, press Alt + Ctrl + Delete, and click Change password. Enter the new password in the New password and Confirm new password fields. Then press OK.
How can I use the Parental Control component in Dr.Web for Windows to limit the amount of time my child can access the Internet or the computer?
- Open the Time tab.
- Use the time grid to create an access schedule.
- Instead of using the calendar, you may choose the option Interval time limit.
A site I want to visit is blocked by the parental control module. How do I exclude this site from the blocking list?
Add the site's address onto the white list, or if you are sure that the site is blocked by mistake, report the false positive to Doctor Web.
At what address can I report false positives of the Dr.Web Parental control?
Send links to web-site mistakenly rated by the module as undesirable to Doctor Web's laboratory via the web-form on our website.
How can I disable the parental control module?
Right-click on the Dr.Web icon in the notification area and select Parental Control → Settings. Enter the password and select Allow access to all sites. In the Local Access tab, select Allow and Unlimited in the corresponding sections. Click Apply to save the changes.
Caution! Disabling Parental control will allow access to all resources on the Internet, LAN and the PC.
How can I recover a lost password to access the Parental control?
There is no way to recover a Parental control access password. The only solution is to import a new password into the registry from a special file.
- Use the download link to obtain the file
- Disable the anti-virus's self-protection
- Double-click on the downloaded file and agree to modify the registry
- Enable self-protection
- Now your password is "drweb" (without the quotes), do not forget to change it in the Parental control settings.
How do I disable access blocking?
Right-click on the Dr.Web icon in the notification area and select Parental Control → Settings. If this is the first launch of the Parental control module, you will need to set a password for it. Then in the subsequent window select what you want to block and then click Apply.
I am prompted to enter a password to access the parental control. What for?
If the password for parental control is not specified, each time you open parental control settings, you will be prompted to set a password. It is Recommended that you set a password right away to prevent unauthorized access to these settings. If no password is required, click Cancel.
I can not turn on the Parental control, it requires a key file. What do I do?
If upon activating the Parental control you receive the message "Unable to find a key file", it means that your license does not cover the Parental control. In this case, it is recommended to remove the component: Go to Start–> Settings–> Control Panel–> Add and Remove Programs, find the Dr.Web anti-virus on the list, click Modify and follow the wizard's instructions to disable this component.
What is the "Local access" option for?
Use the local access settings to restrict access to resources on your computer - files and folders. In addition, it is possible to prohibit the use of removable storage media and access to the LAN. By restricting access to such resources you can avoid damaging or removing sensitive data by a third party and prevent unauthorized access to confidential information.
What is the parental control for?
The Parental control module allows you to restrict users' access to certain sites on the Internet, local files and folders, local network resources. An administrator can manually configure a list of banned sites or take advantage of the constantly updated thematic lists provided by Doctor Web.
When I hover the cursor over the Dr.Web icon in the notification area, the tooltip says that local access protection and URL filtering are disabled. What does this mean and is it dangerous?
Local access protection and the URL filter are parental control features disabled by default. You need to activate them manually by setting the parental control operation mode and access password in its settings.
Which sites can be blocked with the Parental control module?
The Parental control module can restrict acces to any specific sites or web-pages, as well as to all known sites containing information on certain subjects (such as sites about drugs or weapons, sites of paid on-line games, etc.). A list of specific websites to be blocked is set up by the user; both individual addresses and keywords found in URLs can be specified in this block list. Blocking websites by subject is carried out automatically using the lists, updated regularly by Doctor Web.
Will my child be able to disable the Parental control module without my consent?
If you set a password for accessing the Parental Control, only the computer's administrator will be able to do so after entering the password. If no password is set, then any user with administrative privileges will be able to change the settings.
Scanner
What actions сan Dr.Web perform with malicious objects?
If Dr.Web has detected a malicious program, one of the following actions can be applied to it:
Cure — Dr.Web can try to restore the infected file to its original state.
In most cases, the "Cure" option will be unavailable. This action is only available for files infected with known, curable viruses. Trojans and compromised files found in other objects (archives, email files and file containers) cannot be cured.Remove — a malicious object (file, script, email attachment, etc.) is permanently deleted.
Move to quarantine — if for some reason you want to save a file (for example, to send it to Doctor Web’s virus laboratory), you can move it to the secure quarantine folder where it will not be able to harm your PC.
Ignore — no action is taken. Choose this option only if you are completely sure that the threat is in fact a false positive.
Threat-neutralisation options have their limits:
Suspicious objects (seemingly infected files and files that supposedly contain malicious code) cannot be cured.
Threats that are not actually files (e.g., boot sectors) cannot be moved or deleted.
No actions can be performed with individual files in archives, installers or emails—in such cases, an action is applied only to the entire object.
Why is it important to run system scans regularly?
New threats are emerging every day, and it is quite possible for a trojan to get into your system undetected since no corresponding definition yet exists in the virus database and the malware has not done anything suspicious to expose itself. As a result, the file monitor SpIDer Guard, which scans files, whenever they are being opened, launched, or modified, and watches over running processes, cannot detect it.
Dr.Web recommends
Schedule regular system scans to occur at least once a week. You can set up the scans to be run at the most convenient time for you—for example, when you are not using your PC.
What is the scanner designed for? Is SpIDer Guard anti-virus monitor, which always monitors all the calls to files, not enough?
Dr.Web scanner for Windows either scans files at the user’s command or on the schedule specified in the Scheduler. Not all the files are checked, but only those specified in the scanner settings instead. By default, files are checked by format — i.e., files in archives, packed and e-mail files, and RAM and all the autorun objects as well. You may choose to scan disks, folders, scan by file types, by preset mask, or scan all the files. To view current scanner settings, go to the program main window menu bar and select Settings–>Modify settings.
I have installed anti-virus on my PC and run the program. Though I did nothing about it, it started to perform itself — some numbers appeared and the progress bar began sliding to the right in the bottom part of the program window. What is it doing?
Quick scan of the critical system objects with the anti-virus scanner is launched automatically as the program starts. It is required to find out if any viruses exist in the system. After the scan is complete, two right windows indicate numbers. The left one shows the number of viruses found on your PC, while the right one — the number of RAM objects and files scanned with the anti-virus scanner.
How can I enable a scheduled scan?
In order to launch full scan, please use the Task scheduler.
Windows XP:Open the Windows task scheduler (Start->Control panel->Assigned tasks). Find the Dr.Web Daily Scan task pre-installed during installation and open it to edit. In the Task tab, check Enabled. In the Schedule tab, specify scan frequency and time you need. Press Ok to apply the settings. Enter user name and password upon the operating system request.
Windows Vista/7:In order to edit a task pre-installed during the anti-virus installation, right-click on the Dr.Web icon in the notifications area and select Tools->Scheduler. In the next window, select the Drweb Daily Scan task, which is disabled by default. You should enable it (by right-clicking the task and selecting Enable option). In the Triggers tab, edit launch time and frequency.
In the scanner settings, there is an action to process infected and incurable files — Move. Are such files moved to a location on my PC?
The Move action in respect to infected and incurable objects means the following: an object is moved to a special directory specified in the Move to field (by default, it is the infected.!!! subdirectory of the Dr.Web installation directory) and accessible even after the scan is over. Furthermore, after having been moved, the file loses its extension. Such actions mean that the virus is actually “disarmed”, rendered incapable and, therefore, absolutely safe.
Dr.Web anti-spam
How to configure spam filtering to a specific folder in my e-mail client?
To have all the messages marked with Dr.Web spam filter automatically moved to a specific folder — let's call it Spam, for example, — follow the below steps:
- Right-click on the Dr.Web icon in the notifications area and select SpIDer Mail–>Settings. Go to the Anti-spam tab, and check the box next to Add a prefix to the Subject field of e-mails containing spam. In the field below, enter any word or letter combination you like — that's what will be a prefix Dr.Web spam filter will add to the subjects of messages specified to be a spam.
- In your e-mail client, create a folder for spam filtering and configure rule for it so that messages having a prefix you have entered to the Add a prefix to the Subject field of e-mails containing spam be placed into it automatically.
Below are detailed steps on how to set up rules for various e-mail clients. It is assumed that the Anti-spam is configured to mark an incoming spam with the [SPAM] prefix. If you chose an alternative prefix, use it in accordance with this manual...
Microsoft Outlook Express 6
- Create a new folder into which spam will be moved:
- right-click on the account name, and in the context menu select "New Folder...";
- enter the Spam folder name, and click "OK".
- Set a filter rule for messages marked as spam:
- in the menu, select "Tools" - "Rules for messages" - "Mail ...";
- in the first list, check the "Search for messages containing specific words in the "Subject" field;
- in the second list, check the "Move to a specified folder";
- in the "Rule description", click on the "containing specific words";
- enter the [SPAM] key word, and press "Add", then "OK";
- in the "Rule description", click on the "specified";
- select the "Spam" folder created in step 1, and press "OK";
- in the "Rule name", type "Spam filtering", and press "OK" twice.
Microsoft Office Outlook 2003:
- Create a new folder into which spam will be moved:
- right-click on the account name, and in the context menu select "New Folder...";
- enter the Spam folder name, and click "OK".
- Set a filter rule for messages marked as spam:
- in the menu, select "Service" - "Rules and alerts...";
- Go to the "E-mail rules" tab;
- click on "New...";
- select "Create a new rule";
- in Step 1, select the "Check messages upon receipt", then click "Next";
- in Step 1, select "containing
in the "Subject" field; - in Step 2, click on "
"; - in the upper field, enter [SPAM], and press "Add", then "OK" and "Next";
- in Step 1, select "move them to the
folder"; - in Step 2, click on "
"; - select the "Spam" folder created in step 1, and press "OK", then "Next" twice;
- in Step 1, specify the "Spam Filtering" rule name, and click "Finish", then "OK".
Microsoft Office Outlook 2007:
- Create a new folder into which spam will be moved:
- right-click on the account name, and in the context menu select "New Folder...";
- enter the "Spam" folder name, then in the "Folder content" list, select "elements such as Mail"; in the "Place folder into..." tree, choose a location where the "Spam" folder will be stored.
- Set a filter rule for messages marked as spam:
- in the menu, select "Service" - "Rules and alerts...";
- Go to the "E-mail rules" tab;
- click on "New...";
- select "Move all messages containing specific words in the subject field to folder", and click "Next";
- in Step 1, select "containing
in the "Subject" field"; - in Step 2, click on "
"; - in the upper field, enter [SPAM], and press "Add", then "OK" and "Next";
- in Step 1, select "move them to the
folder"; - in Step 2, click on "
"; - select the "Spam" folder created in step 1, and press "OK", then "Next" twice;
- in Step 1, specify the "Spam Filtering" rule name, and click "Finish", then "OK".
Windows Mail 6 (Windows Vista):
- Create a new folder into which spam will be moved:
- right-click on the account name, and in the context menu select "New Folder...";
- enter the "Spam" folder name; in the "Select the folder in which a new folder will be created" tree, select a location where the "Spam" folder wil be stored.
- Set a filter rule for messages marked as spam:
- in the menu, select "Service" - "Message rules " - "Mail...";
- click on "New...";
- in the "1. Select conditions for this rule" list , flag the "Search for messages containing specific words in the "Subject" field";
- in the "2. Select actions for this rule" list, flag the "Move to the specified folder";
- in the "3. Rule Description" field, click on "containing specific words";
- in the "Enter the keywords" dialog box, type [SPAM] in the "Enter keywords or sentence and click" Add"" field, press "Add", then "OK";
- in the "3. Rule Description" field, click on "specified";
- in the next "Move" window, select the "Spam" folder created in step 1, and press "OK";
- in the "4. Rule name" field, type "Spam Filtering" and click "OK" twice.
Ritlabs The Bat! 4
- Create a new folder into which spam will be moved:
- right-click on the account name, and in the context menu select "New" - "New Folder...";
- enter the Spam folder name, and click "OK".
- Set a filter rule for messages marked by anti-spam as spam:
- right-click on the account name, and in the context menu select "Inbox Assistant settings...";
- right-click on the "Incoming mail", and in the context menu, select "New rule";
- in the "Name" field, enter "Spam filter";
- click on "Sender" and choose the "Subject" line from the drop-down list;
- enter [SPAM] into the field after the word "containing"
- under the "Actions" list, click "Add";
- in the drop-down list, select the "Move message to folder";
- in the folder tree, select the "Spam" folder created in step 1, and click "OK" twice.
Mozilla Thunderbird 2.0
- Create a new folder into which spam will be moved:
- right-click on the account name, and in the context menu select "New Folder...";
- enter the Spam folder name, and click "OK".
- Set a filter rule for messages marked by anti-spam as spam:
- select the account name in the tree of accounts and folders;
- in the menu, select "Tools" - "Message Filters...";
- press "Create...";
- in the "Filter name" field, enter "Spam filter";
- in the list below, sequentially select "Subject", then "contains" from the drop-down lists; in the right-hand field, enter [SPAM];
- from the drop-down lists in the list far below, sequentially select "Move message to...", and in the next box, select the "Spam" folder created in step 1, then press "OK";
- close the "Message filters" window.
Which messages are filtered by Dr.Web anti-spam as unwanted?
- To make it short, let’s apply “spam” name to all unsolicited e-mails. The bulk of it comprises advertisements offering different goods and services.
- The most dangerous among spam messages are phishing, pharming and scamming ones. Nigerian scams, lottery and casino scams, fraudulent messages from banks and credit organizations are characteristic of them.
- Next come black political and economic PR scams and the so-called “letters of happiness”.
- There is also a technical spam, or bounce messages, generated by mail servers in reply to undelivered message, whether you did send one or not. Such e-mails might emerge as a result of mail server poor work or virus activity, of some e-mail worm, for instance.
How to activate Dr.Web spam filter?
Incoming mail filtering is processed by SpIDer Mail, one of Dr.Web modules. The following steps describe how to activate the spam filter:
- In SpIDer Mail menu on the Windows Task Panel choose “Settings” – the SpIDer Mail “Settings” window will appear.
- In the “Scan” pane of the SpIDer Mail “Settings” window enable the “Check for the spam” checkbox and press OK to save the changes made; then close SpIDer Mail “Settings” window.
After you’ve activated your spam filter, SpIDer Mail with Vade Retro anti-spam engine integrated into it starts filtering all your incoming mail on POP3 and IMAP4 protocols.
How can spam be filtered into definite mail folder?
To move automatically all messages marked as spam by Dr.Web Anti-spam into definite mail folder in your mail client, do the following.
- In SpIDer Mail menu on the Windows Task Panel choose “Settings” – the SpIDer Mail “Settings” window will appear. Press the “Advanced…” button. The “SpIDer Mail® Spam Settings” window will open. Check the “Add prefix to the subjects of the spam messages” box. Input any word or combination of symbols in the field below it. This will be the prefix Dr.Web Anti-spam will add to subjects of messages marked as spam.
- In the mail client you use, make a new folder for spam. Make the rule for this folder so that all the spam messages with the prefix you specified in the “Add prefix to the subjects of the spam messages” filed are placed there automatically.
How to manage Whitelists\Blacklists?
Whitelists and Blacklists contain mail addresses you either trust or not.
- If the sender’s e-mail address is added to the Whitelist, these messages are not filtered. However, if the sender and the receiver share the same domain name e-mail addresses and this domain name is enlisted in the Whitelist with the “*” symbol, it is filtered for spam.
- All messages enlisted in Blacklist are marked as spam without additional analysis.
Both lists settings should be fill in one after another, parted by “;”. The “*” sign can be used as a part of e-mail address. For example, *@domain.org passes for all addresses with “domain.org” domain name.
Where to forward e-mails falsely marked as spam/non-spam?
In case some messages are falsely filtered, they should be forwarded as attachments to special addresses for analysis and correction of spam-filtering techniques.
- Messages, falsely marked as spam , should be forwarded as attachments to nonspam@drweb.com
- Messages, falsely marked as non-spam , should be forwarded as attachments to spam@drweb.com.
How to avoid filtering Cyrillic e-mails as spam?
At first all spam messages were of Latin origin and spam-filters’ developers, represented for the most part by Western companies, were aimed at filtering these ones only. Later on spammers switched into Cyrillic, too. But since the bulk of spam is still in Latin, there are some difficulties to filter Cyrillic spam.
To save your Cyrillic correspondence from being filtered as spam without a prior analysis, check the “Allow Cyrillic texts” box. Otherwise such e-mails are likely to be marked as spam. “Allow Chinese, Japanese, Korean text” option works the same way.
Dr.Web Firewall
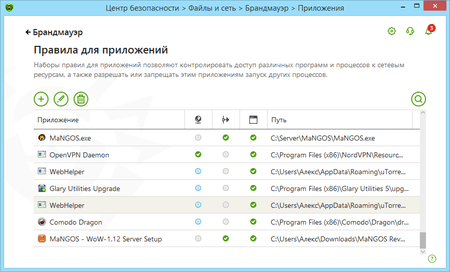
How can I create an application (program) rule in Dr.Web version 8 and earlier?
Right-click on the Dr.Web icon in the notification area. In the menu, hover over the Firewall item and in the drop-down list, select Settings. Click the Application tab.
To create an application rule, click Create. In the opened window, specify the path to the executable file for the program for which you are creating the rule, and select
- the rule type for launching network applications:
- Allow — to allow the application to launch processes.
- Block — to block the application from launching processes.
- Not configured — to customize the selected firewall operating mode for this application.
- and the rule type for accessing network resources:
- Allow all — the application will be permitted to access the network.
- Block all — the application will be blocked from accessing the network.
- Custom — access will be determined by the parameters specified.
- Not configured — to customize the selected firewall operating mode for this application.
You do not need to configure rules manually if the firewall is operating in the training mode — it is easier to configure access for each application right from the firewall notification window when it attempts to connect to the network for the first time.
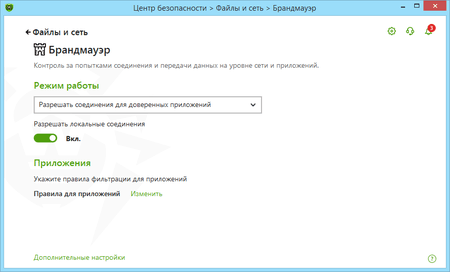
What firewall operational modes are available?
Dr.Web Firewall has four operating modes:
- Allow unknown connections — all unknown connections are allowed. Protection is not active.
- Training mode (create rules for known applications automatically) — learning mode. Rules for known applications are created automatically. The user will be prompted to choose what action to take with all unknown connections.
- Interactive mode — learning mode. When the operating system or an application attempts to connect to a network, the firewall will prompt the user to choose an action.
- Block unknown connections — all unknown connections will be blocked without prompting the user.
Do I need to disable Windows Firewall when installing Dr.Web Firewall?
If you install a Dr.Web package that includes the firewall, you will be prompted to deactivate the Windows firewall. The Windows firewall must be disabled, doing otherwise will result in numerous conflicts that can cause errors or an OS crash.
Neither it is recommended to enable the Windows firewall while the Dr.Web firewall is working.
How do I disable the automatic launch of the firewall at Windows startup?
You can't disable automatic startup for the firewall with standard tools available in the system.. However, you can disable temporarily various anti-virus modules including the firewall at any moment. Right click on the Dr.Web icon in the system tray and select Firewall-> Disable in the context menu.
Note: If the Disable item is not available in the menu, switch to the Administrative mode.
I'm getting messages about new network rules created again and again. How can I disable the notifications?
Dr.Web Firewall in the real time mode creates rules for applications running in the system but are not on its list. Therefore, you must create rules for such applications when they attempt to connect to the network for the first time. A connection request is issued for specific ports and protocols utilized by the application. You can allow all the requested connections, a connection only for a specific protocol and port, or block the connection. Once the rule is created, the firewall handles requests according to the rule and no longer gives out messages regarding application's network activity to the user.
The predefined database contains rules for the most popular programs, as well as all Windows system services and applications. The database is updated on a regular basis.
For more information see the video tutorial on configuring the Dr.Web firewall.
What’s the firewall?
The firewall is a program that controls the exchange of data between your PC and the rest of the network. The firewall's main job is to monitor application-generated network activity and prevent hackers or malicious programs from trying to send information from your PC to the network or, vice versa, to accept it from a remote source without authorisation.
What is the firewall’s interactive mode?
In this mode, the firewall can be trained to respond to attempts made by programs to access the Internet.
Upon detecting programs making attempts to access network resources, Dr.Web Firewall checks whether filtering rules have been set for those programs. If the rules haven’t been specified, the user is prompted to either choose a single action for the firewall or create a rule that will be used in the future to process such an application's network activity.
The firewall has blocked access to the Internet. What should I do?
If the firewall is blocking your ability to work with the network, you need to do the following:
-
To reset the settings, click on the Dr.Web icon in the system tray, and in the Dr.Web menu, select Security Center. Click on the
 icon in the lower-left corner of the window, and then on —
icon in the lower-left corner of the window, and then on —  in the upper-right corner. In the Manage settings section, select Change → Restore defaults, and click on OK.
in the upper-right corner. In the Manage settings section, select Change → Restore defaults, and click on OK.
Important! This action will reset all of the user settings for all the Dr.Web components, and you will need to configure them again.
After that, when you try to access the Internet, you may see requests from the firewall (to create a rule, to block once, to allow once). Create allow rules for selected applications by clicking on the button Create rule → Allow → OK.
For more on how to train the firewall, refer to the documentation
-
Please contact our technical support service. Attach the report created by the DwSysInfo utility to your request.
To generate a report:
- Download and save the utility on your PC: https://download.geo.drweb.com/pub/drweb/tools/dwsysinfo.exe
- Launch the saved dwsysinfo.exe file.
- Click on the Generate report button.
- Wait for the report-generation process to complete.
How can I prevent a program from connecting to the Internet?
To prevent a specific program from connecting to the Internet, create a new rule. Click the Dr.Web icon on the taskbar, and select Security Center → Files and Network. Click on the ![]() icon.
icon.
In the UAC dialogue, click on Yes, and enter the administrator password, if necessary.
Select the Firewall section, and click on Change in the Application rules.
In the newly appeared window, click on the ![]() icon to add a new rule.
icon to add a new rule.
In the next window, enter the path to the application's executable file, and in the drop-down list Launching network applications, select Block. Then select Block all on the Access to network resources list.
Click on OK to have your changes go into effect.
A firewall notification window has appeared. What should I do?
The notification window’s appearance indicates that a processing rule has not been set for the application to which the firewall has reacted. You can do one of the following:
- Allow once — the application’s network activity is allowed for the duration of the current session. After the PC is restarted or you want to use the program again, the firewall will prompt you to allow the Internet connection again.
- Block once — this blocks the program’s network activity. Only for the current session.
- Create rule — when you configure a rule for an application, the firewall will automatically follow this rule. By selecting this option, you will see a window that lets you choose a course of action:
- Allow network connections for the application on port *port number*
- Block network connections for the application on port *port number*
- Allow all network connections
- Block all network connections
- Create custom rule — you can create a new firewall rule for the current program.
Note. Always try to create rules to automate the firewall's operation.
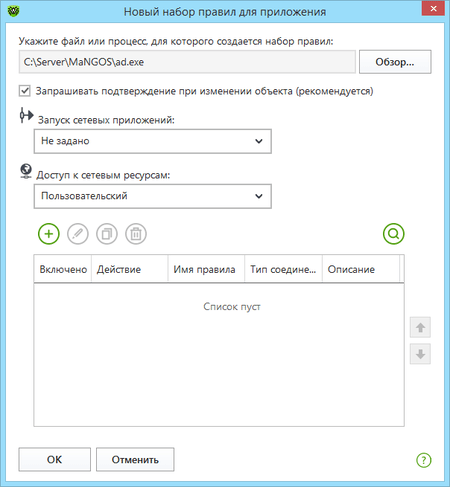
How can I create a rule for an application (program)?
To prevent a specific program from connecting to the Internet, you have to create a new rule. Click on the Dr.Web icon on the taskbar, select Security Center → Files and Network and click on the ![]() .
.
In the UAC dialogue, click on Yes, and enter the administrator password, if necessary.
Select the Firewall section, and click on Change in the Application rules.
In the newly appeared window, click on the ![]() icon to add a new rule.
icon to add a new rule.
In the next window, enter the path to the application's executable file, and then in the drop-down list Launching network applications, select the action you need:
- Allow — when you try to run the network application, the firewall will allow this action.
- Block — when you try to run the network application, the firewall will block this action.
- Not specified — when you try to run the network application, the firewall will issue a request.
Then select the action you need from the Access to network resources list:
- Allow all — any network activity will be allowed for the program.
- Block all — any network activity will be blocked for the program.
- Custom — you can manually configure all the parameters for the program’s network activity.
- Not specified — every time the program tries to access the Internet, the firewall will issue a request before connecting.
Click OK to have your changes go into effect.
If the firewall is operating in interactive mode, there is no need to manually configure rules — it is easier to configure access for each application at the time of its initial network activity, directly from the firewall notification window.
How can I disable the firewall?
Click on the Dr.Web icon on the taskbar, select Security Center → Files and Network, and click on the ![]() icon. In the UAC dialogue, click on Yes, and enter the administrator password, if necessary.
icon. In the UAC dialogue, click on Yes, and enter the administrator password, if necessary.
Then, toggle on the switch to make the Firewall component active — its frame will turn red.
How can I reset the firewall settings?
To reset the settings, click on the Dr.Web icon in the system tray. In the Dr.Web menu, select Security Center. Click on the ![]() icon in the lower-left corner of the window, and then on
icon in the lower-left corner of the window, and then on ![]() — in the upper-right corner. In the Manage settings section, select Change → Restore defaults, and click on OK.
— in the upper-right corner. In the Manage settings section, select Change → Restore defaults, and click on OK.
Important! This action will reset all the user settings for all the Dr.Web components, and you will need to configure them again.
What firewall operational modes are available?
Dr.Web Firewall has three operating modes:
- Allow unknown connections — all unknown connections are allowed. Protection is not active.
- Allow connections for trusted applications — rules for known applications (with a valid digital signature) are created automatically. The user will be prompted to choose what action to take with all unknown connections.
- Interactive mode — learning mode. When the operating system or an application attempts to connect to the network, the firewall will prompt the user to choose an action.
- Block unknown connections — all unknown connections will be blocked without prompting the user.
The user can configure the mode in the firewall's settings. If a rule has already been set for an application, the firewall will follow it.
What is a parent process?
A parent process is a process or an application that can run other applications. Users can configure rules for parent processes in the window used to create or edit rules for an application with the help of the drop-down list Launching network applications.
How can I configure rules for network connections?
Click on the Dr.Web icon on the taskbar, select Security Center → Files and Network, and click on the ![]() icon. In the UAC dialogue, click on Yes, and enter the administrator password, if necessary.
icon. In the UAC dialogue, click on Yes, and enter the administrator password, if necessary.
Select the Firewall section, and click on Show additional settings. In the Operation parameters for known networks section, click on Change. In the next window, the user can define a set of predefined rules for each network connection.
- Allow all — all packets are allowed.
- Block all — all packets are blocked.
- Default rule — rules that describe the most popular network configurations and common attacks (used for all interfaces by default).
Where can I find the firewall report?
What is a packet filter?
This firewall element manages the traffic flow via the selected protocols by allowing or blocking packets according to specified conditions. The packet filter is a basic means of ensuring your computer’s security; it operates independently of applications.
Can I install the firewall without installing the Dr.Web anti-virus?
Dr.Web Firewall is a Dr.Web anti-virus software component, and it is impossible to install the firewall without the anti-virus.
What does "Digital signature - Unknown" mean when an application attempts to access the Internet? What is a digital signature? And what does it affect?
A digital signature is a code that verifies that a program has been received from a particular source and has not been changed. At the same time, a signed application is not necessarily secure, so users should be careful when installing any software, even signed software.
An unknown application is constantly trying to access the Internet. What could this mean? And what should I do in this situation?
This could be malware. It is recommended that you launch a full anti-virus system scan.
Do I need to configure a packet filter for my home PC?
At home, when you need to protect only one computer against network attacks, the packet filter configuration is not required. The fact is that the firewall database contains a substantial number of rules, and these rules are activated as they are required. If, for any reason, a rule is absent, the firewall will request the action.
SpIDer Guard
What actions сan Dr.Web perform with malicious objects?
If Dr.Web has detected a malicious program, one of the following actions can be applied to it:
Cure — Dr.Web can try to restore the infected file to its original state.
In most cases, the "Cure" option will be unavailable. This action is only available for files infected with known, curable viruses. Trojans and compromised files found in other objects (archives, email files and file containers) cannot be cured.Remove — a malicious object (file, script, email attachment, etc.) is permanently deleted.
Move to quarantine — if for some reason you want to save a file (for example, to send it to Doctor Web’s virus laboratory), you can move it to the secure quarantine folder where it will not be able to harm your PC.
Ignore — no action is taken. Choose this option only if you are completely sure that the threat is in fact a false positive.
Threat-neutralisation options have their limits:
Suspicious objects (seemingly infected files and files that supposedly contain malicious code) cannot be cured.
Threats that are not actually files (e.g., boot sectors) cannot be moved or deleted.
No actions can be performed with individual files in archives, installers or emails—in such cases, an action is applied only to the entire object.
Can I temporarily disable SpIDer Guard with no need to reboot my PC?
Yes, you can. In order to disable SpIDer Guard, right-click on the Dr.Web icon in the notifications area and select SpIDer Guard–>Disable.
What is the function of the Block removable media autorun option?
Enabling this option allows to block automatic launch of autorun.exe-like files from removable media and hard disk drives. This option is used to neutralize autorun-viruses, which are automatically activated when a device is connected to the PC with autorun option enabled.
What is Prohibit Host system file modification option used for?
Enabling this option allows to block attempts to modify HOSTS system file used by operating system to make an Internet access easier. Modifications of this file may be resulted in virus or any other malicious program activities, and this may cause loss of access to some websites or network resources as a whole.
What are the SpIDer Guard functions?
Anti-virus guard is loaded into RAM and checks files being created or modified on the hard disk and all the files being opened on network disks and removable media “on the fly”.
Besides, SpIDer Guard constantly traces running processes activities specific to viruses and blocks those processes upon their detection.
Upon detection of infected objects, SpIDer Guard interacts with them according to the specified settings.
Where is SpIDer Guard log located?
SpIDer Guard log file is called spiderg3.log and located in the anti-virus installation folder (by default, it is C:\Program Files\DrWeb).
What does “Paranoid mode” mean?
Paranoid mode is an enhanced protection mode. When this mode is activated, the guard starts scanning all the files being opened, created or modified on hard disks, removable media and network disks.
What does “Optimal mode” mean?
In the Optimal mode the guard scans only files being launched, created and modified on hard disks, removable media and network disks.
How can I add an exclusion for the SpIDer Guard scan?
In order to exclude a program or file from the SpIDer Guard scan, right-click on the Dr.Web icon in the notifications area and select SpIDer Guard–>Settings. In the next window, proceed to the Exclusions tab, press the Browse button to select the folder where the program to be excluded from the scan is installed, and press Add.
Should it become necessary to exclude a folder or file while the Dr.Web for Windows Scanner is running — select Settings–>Modify settings in the scanner menu. You may add a folder in the Scan–>Excluded paths list tab, and a certain file in the Excluded files list, then you need to press Add.
SpIDer Mail
I read my emails via a browser. Does the SpIDer Mail component check email messages for viruses and spam?
SpIDer Mail scans email messages only if you are using a local mail client (for example, MS Outlook, Mozilla Thunderbird, etc.). Moreover, emails are scanned as they are downloaded. When the list of new messages is displayed on the server, they may not yet have been physically downloaded by you, and, thus, at that moment, they are still unscanned.
If an email is opened via a browser, it is not downloaded to the local computer. Instead, it is rendered by the browser according to the message located on the remote server. It is impossible to scan an email if it is not fully downloaded. But any attachments you save from an email message on the disk of your computer will be scanned by SpIDer Guard.
Which addresses shall I use to send letters to if misrecognized as a spam / not spam?
If the spam filter misrecognizes some letters, they can be forwarded to special mail addresses for analysis and improving filter performance quality:
- Send letters misrecognized as a spam to nonspam@drweb.com.
- Send letters not recognized by mistake as a spam to spam@drweb.com.
Important! You should forward messages as attachment, not as inline.
How can I test SpIDer Mail performance?
You can test proper operability of anti-virus programs detecting viruses by their signatures with the use of EICAR (European Institute for Computer Anti-Virus Research) file.
This program is specially designed to allow you to see how the installed anti-virus will alert you to the viruses it detected, with no need to expose your PC to danger. Eicar program is not malicious but is specially tuned so that most anti-viruses treat it as a virus. Dr.Web refers to this “virus” as EICAR Test File (Not a Virus!).
To test mail anti-virus performance, you can ask a friend of yours to send you this file, or otherwise try to send it to yourself. If SpIDer Mail detects a virus — that is OK.
Nothing found